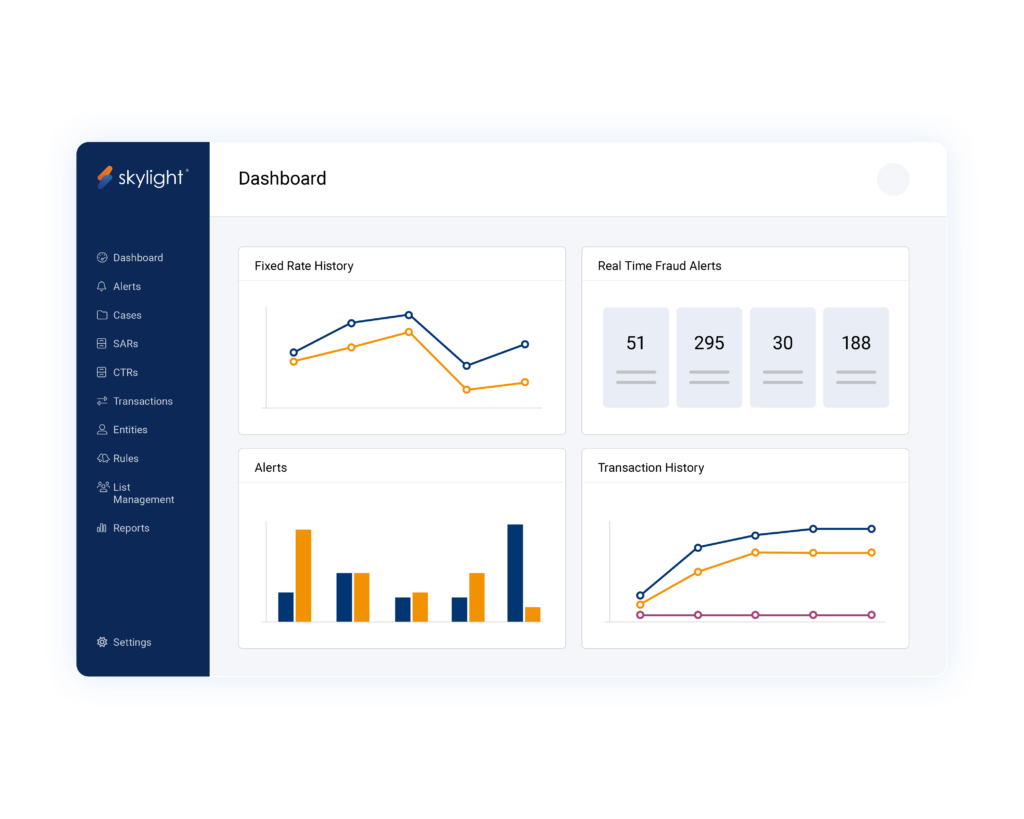
Real‑Time
Prevent fraud in real time with our AI fraud detection software. Boost accuracy and streamline investigations by leveraging Skylight’s powerful, explainable AI technology and collective intelligence network.
Fraud Typologies
Involves the unauthorized use of payment methods like credit cards, debit cards, or online systems for fraudulent transactions. These common types of payment fraud can lead to significant financial losses, chargebacks, and reputational damage for businesses, as well as inconvenience and financial harm to consumers.
- Credit Card Fraud: Stealing card information through skimming, phishing, or hacking to make unauthorized purchases.
- Card-Not-Present (CNP) Fraud: Using stolen card information for online or phone transactions without needing the physical card.
- ACH and Wire Transfer Fraud: Gaining unauthorized access to bank accounts to initiate electronic transfers or wire money.
- Chargeback Fraud: Disputing legitimate charges as unauthorized to get refunds while keeping the products or services, also known as “friendly fraud.”
Detect payment fraud with high precision and in real-time using our full AI fraud detection software suite of identity services, global network intelligence, and AI tools.
Occurs when a malicious actor gains unauthorized access to a victim’s online account through methods like phishing or credential stuffing. Once in control, the fraudster can make unauthorized purchases, transfer funds, or steal personal information, often for financial gain or identity theft. Victims usually realize the fraud too late, resulting in financial losses and compromised data.
Combining machine learning, anomaly detection, geolocation, and behavioral analyses can help detect high-risk sessions and prevent most fraudulent logins.
Involves creating a fake identity by combining real and fabricated information, such as a real social security number paired with a fake name and address. Fraudsters use this identity to open accounts and build credit with small purchases and repayments before maxing out credit limits and disappearing.
This fraud is challenging to detect as the fake identity doesn’t match any real individual, making it a growing threat that leaves organizations with significant losses.
Detect synthetic IDs before they cause losses by scrutinizing identity factors at account creation and leveraging our global transaction network to identify high-risk synthetic identity thieves.
Involves cybercriminals impersonating company figures via email to deceive employees into transferring funds or sharing sensitive information. They use tactics like phishing or spoofing to appear legitimate, leading to significant financial losses and data breaches.
Leverage immediate alerts and risk scores generated in real-time using machine learning, customizable rules, and our global anti-fraud network to identify trusted and untrusted emails, automate workflows, and more.
Occurs when a fraudster uses stolen or fake information to apply for financial products like credit cards, loans, or bank accounts. They might use a real person’s identity (identity theft) or create a fake one (synthetic identity fraud). This can lead to significant financial losses for both the victim and the financial institution.
Prevent this type of fraud through vital early identification using our device and behavioral fingerprinting, anomaly detection, network analyses, and machine learning.
Involves secret cooperation between parties to deceive an organization or individual for financial gain. This often includes employees or partners manipulating processes and falsifying records. They commonly create multiple layers of deception and cover-up actions that make it hard to detect, leading to significant financial and reputational damage.
Prevent significant losses using Skylight’s machine learning and velocity triggers to detect and halt these schemes early.
Involves exploiting vulnerabilities in mobile devices, apps, or networks to commit fraudulent activities. This type of fraud can take various forms:
- SIM Swapping: Fraudsters trick or bribe mobile carriers into transferring a victim’s phone number to a new SIM card. Once they control the number, they can bypass two-factor authentication and gain access to banking, email, and social media accounts.
- Mobile Malware: Cybercriminals distribute malicious software through apps or phishing links. Once installed, the malware can steal sensitive information, track activities, or take control of the device.
- Smishing (SMS Phishing): Fraudsters send text messages pretending to be legitimate companies or institutions to trick recipients into clicking on malicious links or providing personal information.
- Mobile Payment Fraud: This occurs when fraudsters exploit vulnerabilities in mobile payment systems, such as mobile wallets or payment apps, to make unauthorized transactions or steal financial information.
Bolster your mobile fraud detection through a combination of our device fingerprinting, behavioral biometrics, machine learning, and enterprise analytics.
Involves unauthorized use or manipulation of gift cards, loyalty, and reward programs for financial gain. As points and gift cards are often dispensed more freely than physical products, these frauds cause significant financial losses and damage trust in the programs.
- Gift Card Fraud: Fraudsters may steal or purchase gift cards for unauthorized use, resale, or exploitation of system vulnerabilities to drain balances or create counterfeit cards.
- Loyalty and Rewards Fraud: Criminals may manipulate programs through hacking, creating fake accounts, or exploiting program loopholes to steal points, miles, or rewards to sell for profit or redeem for products and services.
Control these risks effectively by combining a thoughtful purchaser data request strategy with our advanced data analysis and machine learning.
Other fraud typologies supported by our AI fraud detection software include:
- Call Center Fraud
- Loan & Credit Fraud
- Marketing & Affiliate Fraud
- Return Fraud
- Insider Threats
- Know Your Vendor (KYV)
Powerful Technologies
Artificial Intelligence
Streamline investigations confidently with explainable models
Machine Learning
Streamline investigations confidently with explainable models

Collective Intelligence Network
Enrich your customer data with powerful global insights
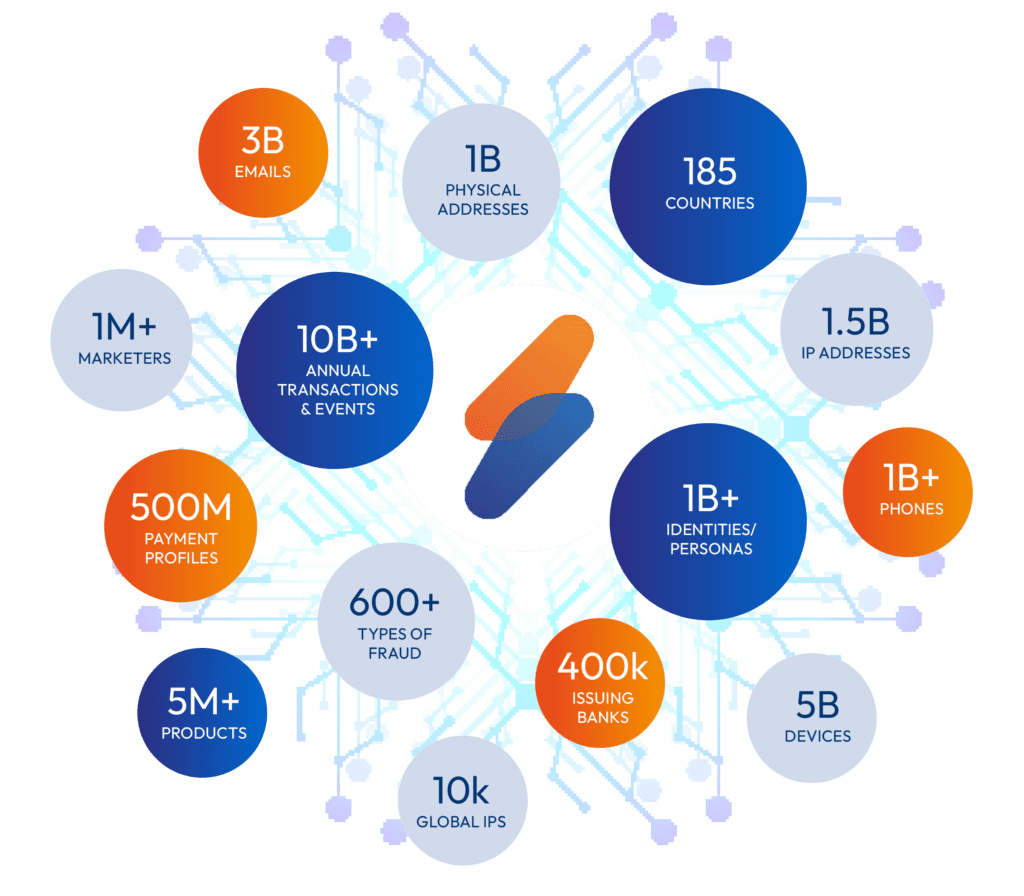
Real-Time Risk Scoring
Make intelligent, data-driven decisions faster
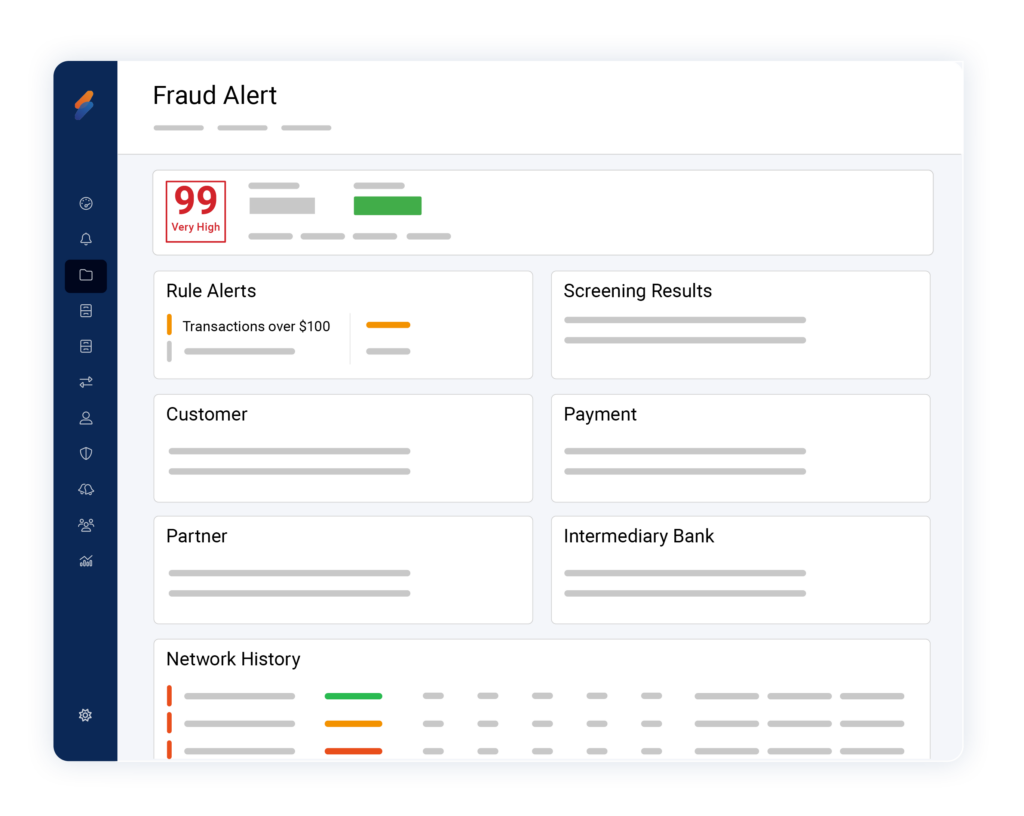
Flexible Scoring Settings
Configure risk scoring categories to your unique tolerance level
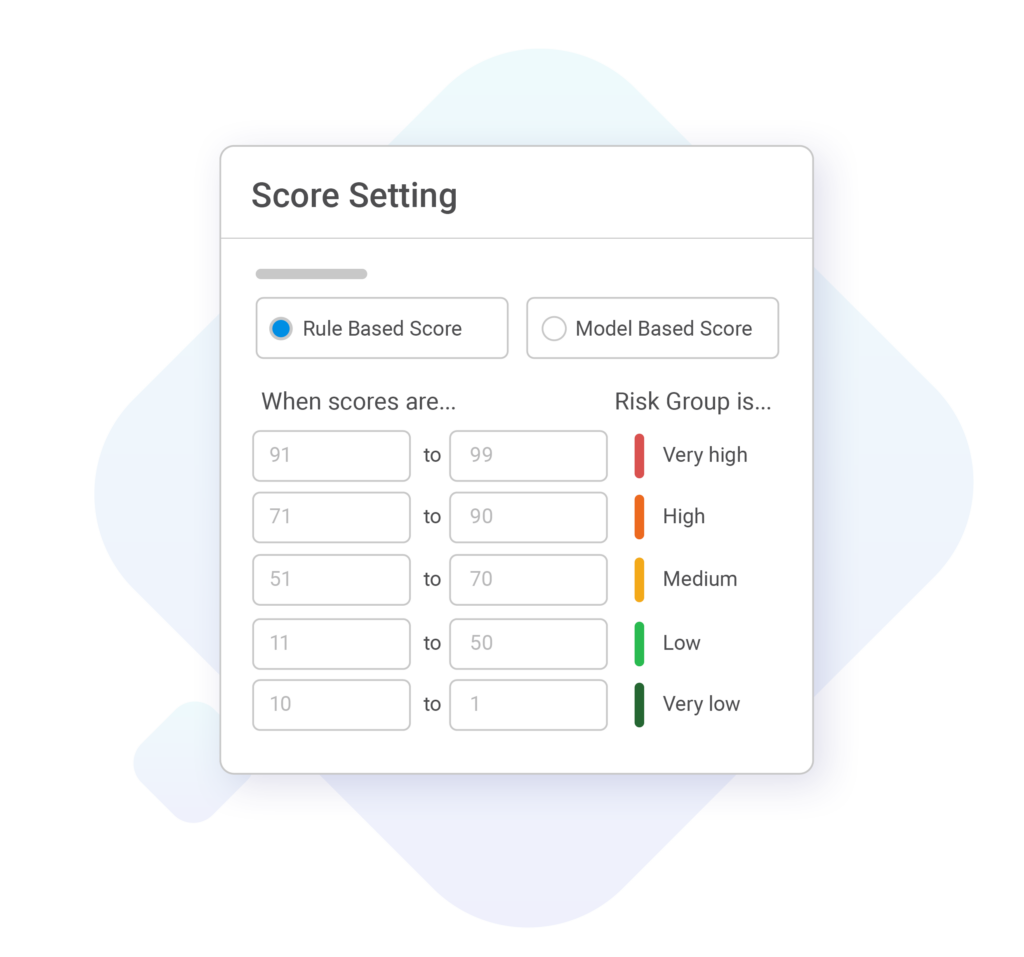
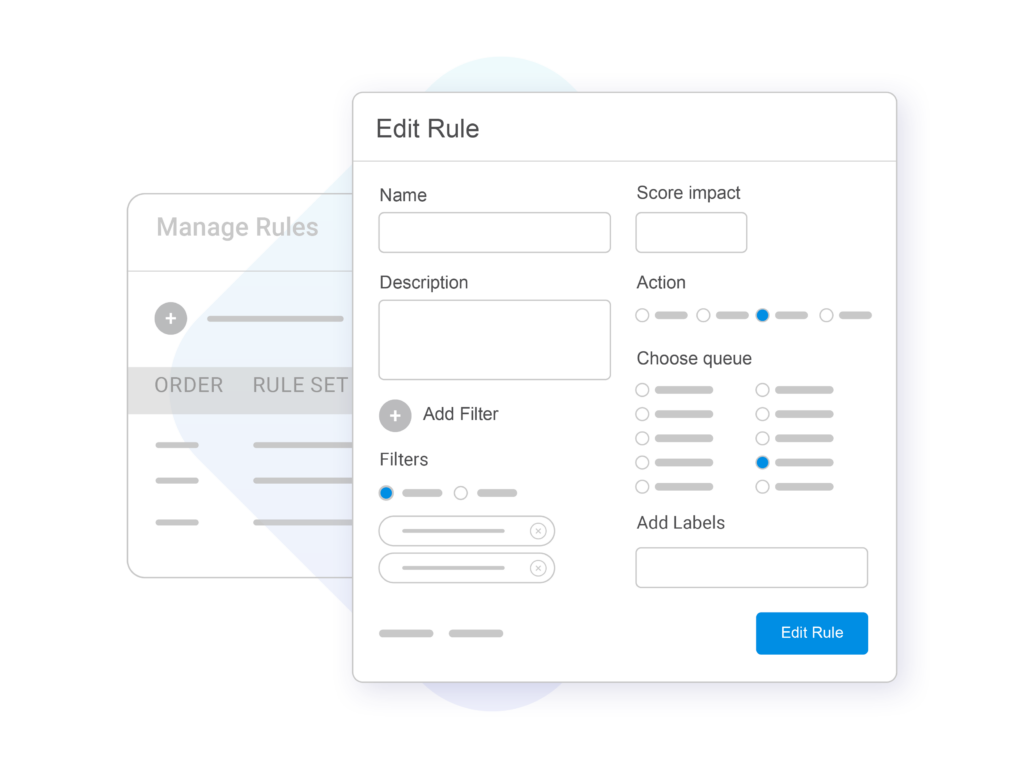
Rules Engine
Unlock comprehensive and flexible rule-creation options
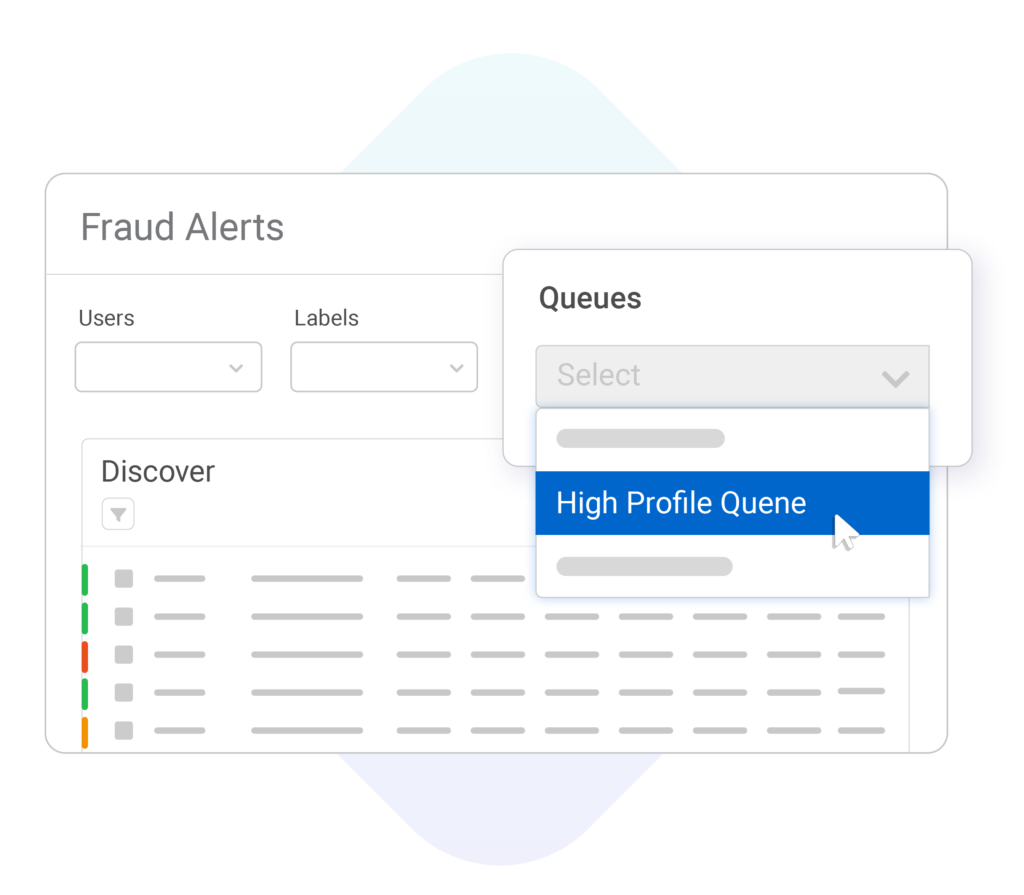
Teams & Queues
Boost productivity with smart alert segmentation options
Denial List
Stop known bad actors in real-time
Dashboards
Make more informed decisions based on real-time insights
Case Management & AI Technology
Skylight combines intuitive case management tools with advanced AI to streamline your workflows. Our integrated platform helps teams work faster, smarter, and with greater confidence across the entire case lifecycle.
Case Management
Streamline your AML program with integrated Case Management
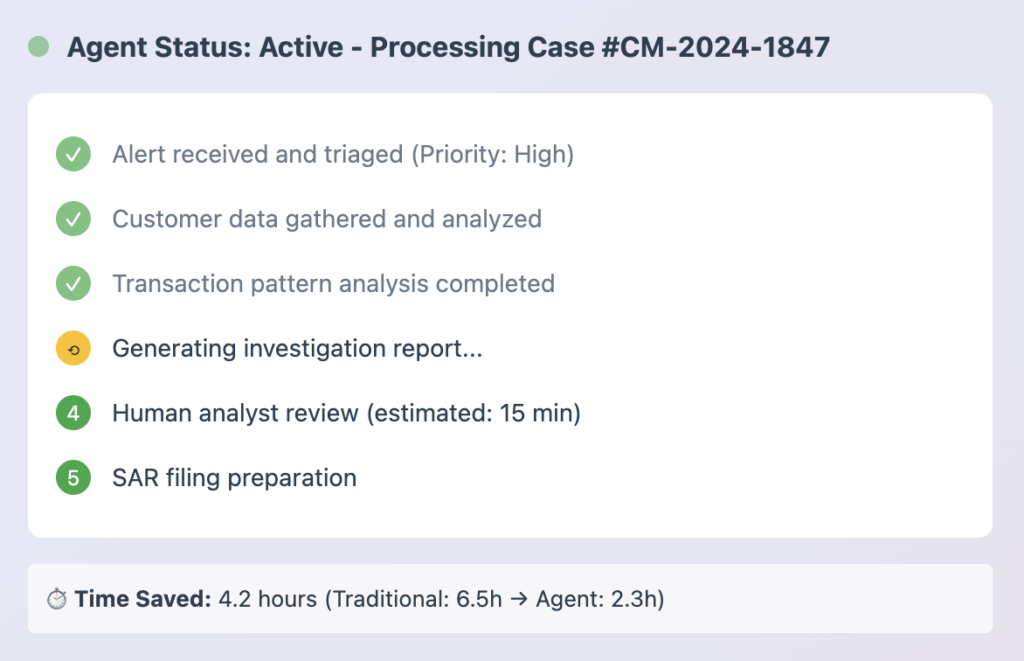
Artificial Intelligence
Increase efficiencies with Skylight’s powerful AI
Grow with Skylight
Unified FRAML Platform
Skylight’s Real-Time Fraud Detection Module with our full suite to experience the benefits of a seamlessly integrated fraud and AML solution, including increased efficiency, holistic insights, and seamless collaboration across your risk and compliance teams.